Sniffing is an action where a user can eavesdrop on the activities and network traffic of the target. Sniffing can be executed by using the tcpdump command in Kali Linux. Using two Kali Linux Virtual Machine (VM), it is possible to test this sniffing method. The first VM is going to be used as the target while the other VM is used to attack the target VM. This tutorial will be using Virtual Box in Windows 10 and running kali-linux 64bit.
These are the steps to sniff a computer’s internet activity:
- On the Virtual Box (Vbox) settings, configure both Kali Linux VM Network settings from NAT to Bridged Adapter.
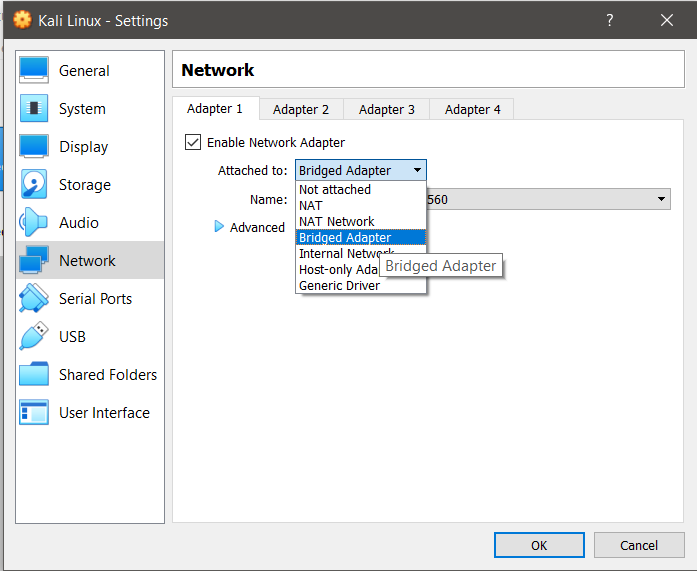
- Under the Network Settings of Vbox, click on Advanced and reset the MAC address of both VMs.
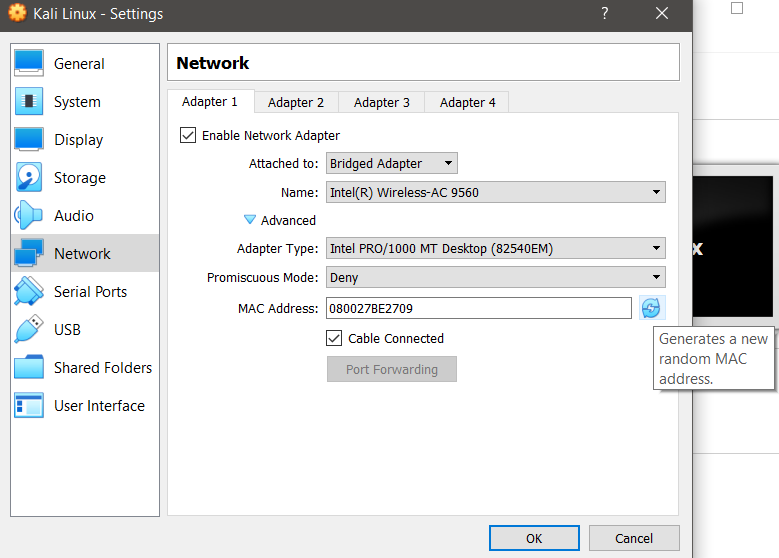
- Confirm the changes to network settings on both VMs. These edits are to ensure that the Kali Linux does not have the same IP address as one another.
- Afterwards connect your device to either a Wifi Adapter, hotspot or a network which is compatible Bridged Adapter.
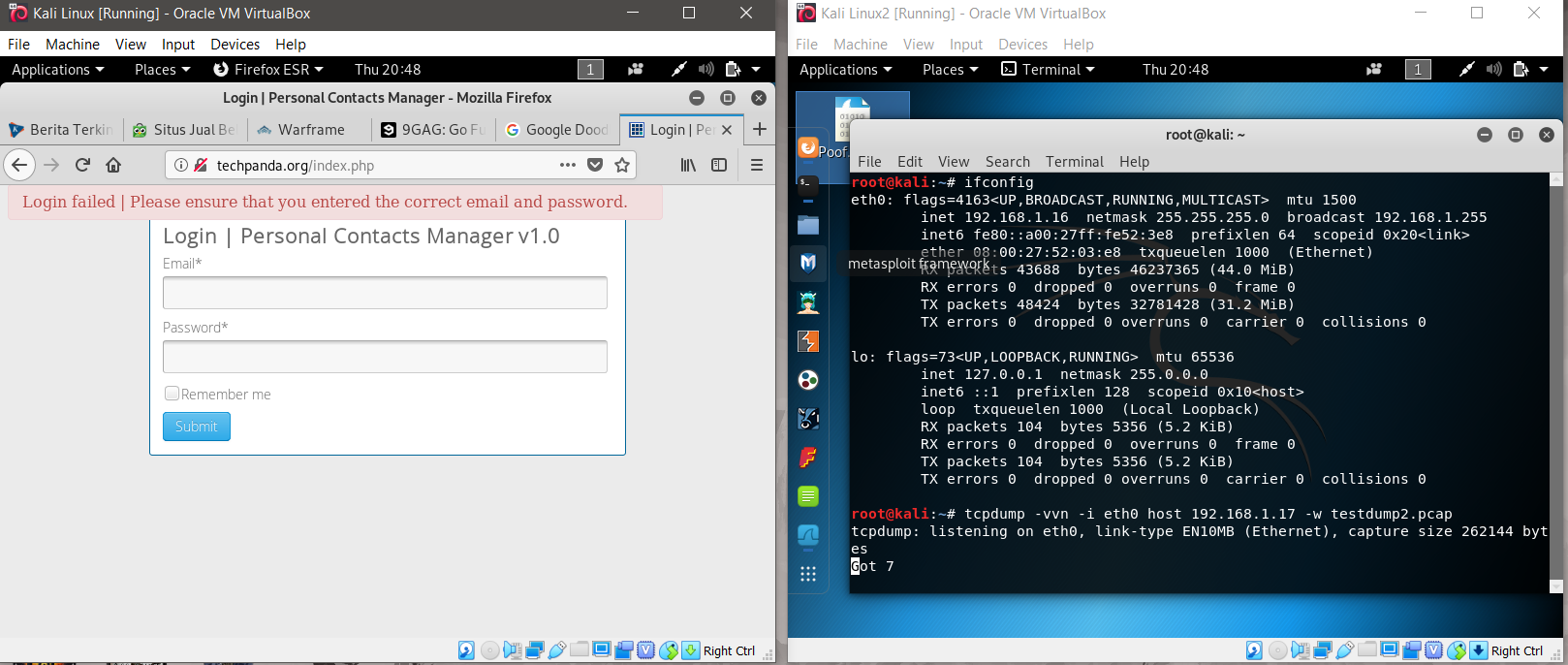
- Once you run both Virtual Machines, in the target VM, open terminal and type the command ifconfig and extract the target VM’s IP address.
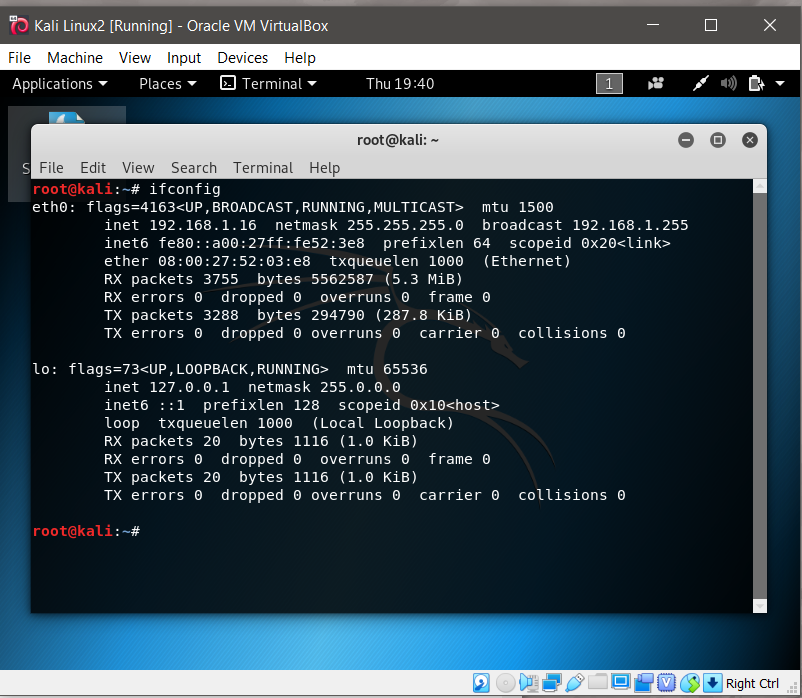
ifconfig command
- In the attacking VM, open the terminal in input the command tcpdump -w eth0 host [target ip address] -w filename.pcap. The tcpdump command work similarly to WireShark as it can detect network traffic of a device. The command can capture how many request it Got.
- For example: tcpdump -w eth0 host 192.168.31.34 -w testdump.pcap
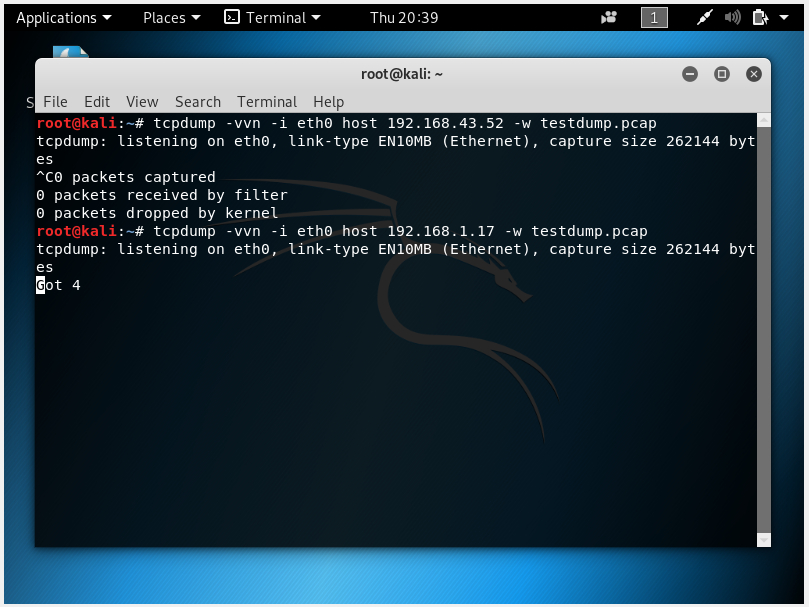
- For example: tcpdump -w eth0 host 192.168.31.34 -w testdump.pcap
- On the targeted VM, browse through the internet and open up websites you normally browse such as Google, Twitter, etc.
- After browsing for a designated amount of time, stop the tcpdump command by pressing Ctrl + C on the terminal.
- Open the filename.pcap file on your root folder.
Result:
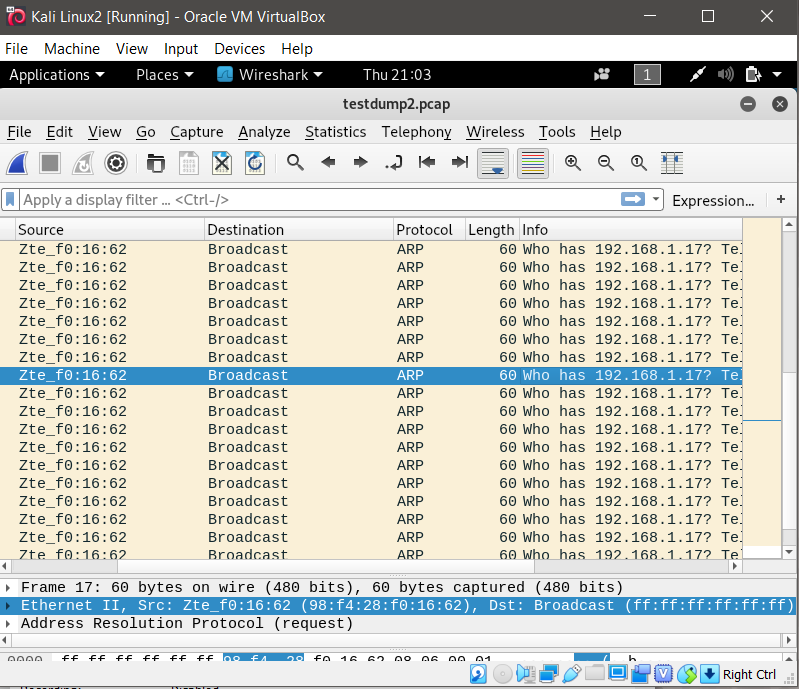
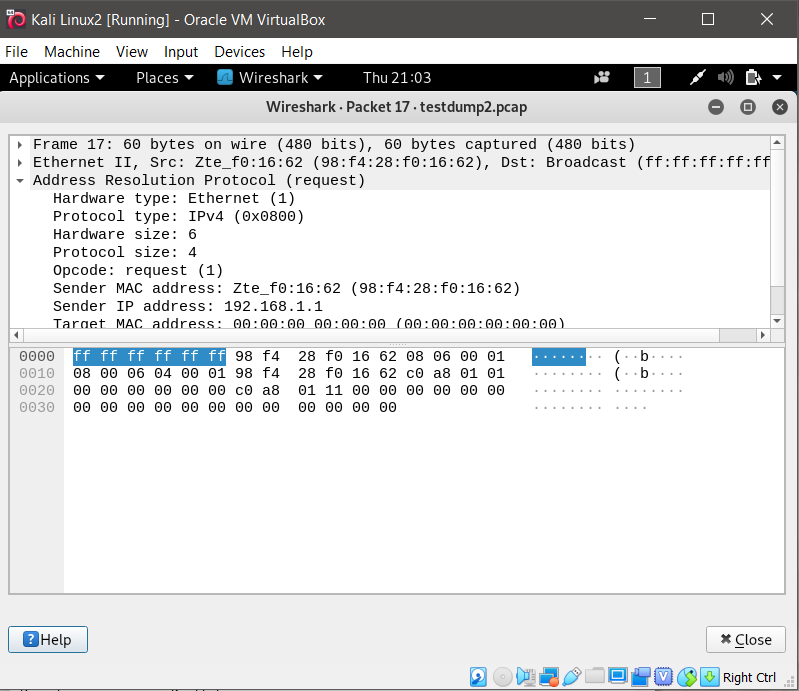
Based on the result, the command was able to track how many packets it has captured when the target browse through the internet, but however it did not capture the specific activities the target has browsed on their browser.
